OpenStack: Fix Security Group Enforcement on Compute Nodes
I discovered the instances in my home lab were not being protected by the neutron security groups I’d set up for them - what followed was a week-long odyssey to discover the culprit. IPTables rules were being put in place, and every other aspect of Neutron networking was just fine. Making things more mysterious, a test deploy on my own desktop, with the host running Fedora 23 and the containers running CentOS 7, did not manifest the issue. [caption id="" align=“aligncenter” width=“609”]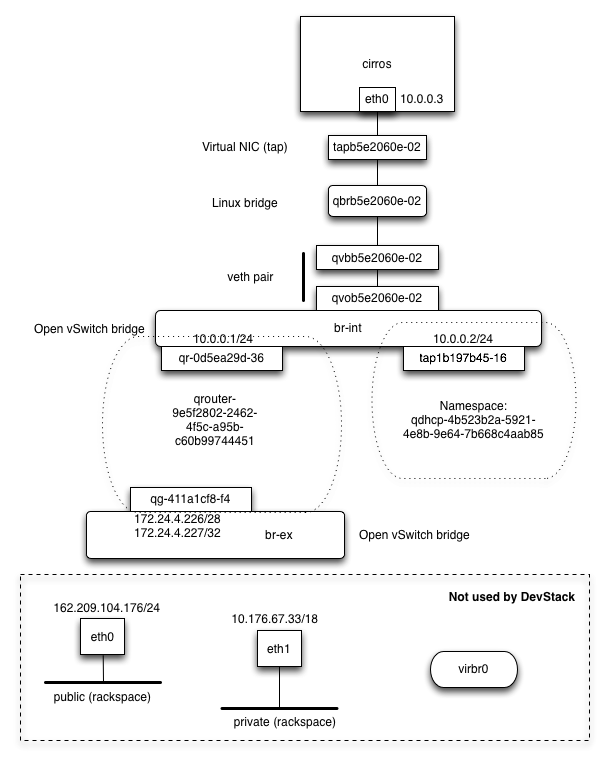 A handy diagram from the excellent “OpenStack Hackspace” - click image to check it out.[/caption]
A handy diagram from the excellent “OpenStack Hackspace” - click image to check it out.[/caption]
Security groups are applied to the tap interface closest to the virtual machine, shown above (not mine - click the image to see the rest of that excellent tutorial).
It turns out there’s a pair of kernel tunables that govern whether or not iptables rules are applied to interfaces that are members of a bridge, as in this instance. It also turns out that Red Hat, for some reason, toggled the default value of this tunable to 0 after RHEL 7 was released.
These tunables, and their required values, are:
net.bridge.bridge-nf-call-iptables = 1
net.bridge.bridge-nf-call-ip6tables = 1
And this needs to be set on the outer host, if you run your OpenStack cloud in containers. If not and/or otherwise, you need this set on your compute nodes as this is where security groups are set.
Hope this saves someone a week of troubleshooting! :-)
